The world of cybersecurity is constantly evolving and the need for advanced security measures has become more important than ever before. One of the most popular and effective tools used by businesses today is Security Information and Event Management (SIEM). However, some experts in the industry have claimed that SIEM is dead, citing the emergence of newer technologies and strategies.
While it’s true that there are newer approaches to cybersecurity, it’s important to note that SIEM remains a crucial component of an organization’s overall security framework. In fact, over the last five years, major tech companies such as Microsoft and Google have entered the SIEM market, which clearly indicates that there is still significant demand for this technology.
Microsoft, for example, recently launched their Azure Sentinel SIEM solution. This platform is designed to help organizations detect and respond to threats quickly and efficiently by analyzing data from various sources, including user devices, applications, and cloud infrastructure. Similarly, Google’s Chronicle platform is also a SIEM tool that provides advanced threat detection and analysis capabilities.
The fact that major tech companies like Microsoft and Google are investing in SIEM technology demonstrates its continued relevance and importance in the industry. These companies have recognized the value of SIEM solutions in providing better security for businesses of all sizes.
Moreover, end-users also seem to believe that SIEM is far from dead. In a recent survey conducted by Cybersecurity Insiders, 87% of respondents stated that they plan to either maintain or increase their SIEM spending in the coming year. This indicates that organizations are still heavily relying on SIEM technology to protect their networks and assets from potential cyber threats.
In conclusion, while some experts may claim that SIEM is no longer relevant, the evidence shows otherwise. The continued investment and adoption of SIEM by major tech companies and end-users alike prove that SIEM is still very much alive and an essential component of an organization’s cybersecurity strategy. So, instead of asking whether SIEM is dead, the question should be how can we continue to improve and optimize this important technology to keep pace with evolving cyber threats.

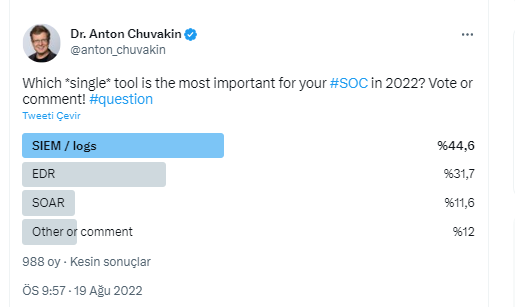
Let me respond to those who say XDR has ended SIEM with a quote from Anton Chuvakin.

Let me give you another survey result about XDR and SIEM.
SIEM is a security system that detects many different types of attacks. Some examples may include:
- Malware attacks: SIEM can detect malware attacks by analyzing the behavior of the system and network traffic. It can also detect and alert on suspicious files or processes that may indicate a malware infection.
- Denial-of-Service (DoS) attacks: SIEM can identify and alert on DoS attacks by analyzing network traffic patterns and detecting unusual traffic spikes or patterns that may indicate an attack.
- Advanced persistent threats (APTs): SIEM can detect APTs by correlating events across multiple systems and identifying patterns of suspicious behavior that may indicate an ongoing attack.
- Phishing attacks: SIEM can detect and alert on phishing attacks by monitoring email traffic and identifying suspicious links or attachments.
- Unauthorized access attempts: SIEM can detect unauthorized access attempts by monitoring login activity and alerting on suspicious activity such as failed login attempts, brute force attacks, and login attempts Insider misuse from unusual locations.
- Insider misuse: SIEM can detect when authorized users misuse their access privileges, such as accessing sensitive data they don’t need to perform their duties, or performing unauthorized activities on the network.
- Ransomware attacks: SIEM can detect ransomware attacks by analyzing system and network activity, such as the sudden encryption of files, or the appearance of ransom notes.
- Data exfiltration: SIEM can detect when data is being exfiltrated from the network, either through malicious actions or inadvertent leaks, by monitoring network traffic and user activity.
- Social engineering attacks: SIEM can detect social engineering attacks, such as spear-phishing, by analyzing email activity, identifying suspicious emails, and alerting security teams to potential threats.
- Web application attacks: SIEM can detect attacks targeting web applications, such as SQL injection or cross-site scripting, by analyzing application logs and network traffic.
- Brute-force attacks: SIEM can detect brute-force attacks by monitoring login activity and identifying repeated attempts to log in with incorrect credentials.
- Command and control (C&C) communications: SIEM can detect C&C communications used by attackers to remotely control compromised systems, by analyzing network traffic and identifying suspicious communication patterns.
- Network scanning: SIEM can detect when attackers scan the network looking for vulnerabilities, by analyzing network traffic and identifying patterns of suspicious behavior.
- Privilege escalation: SIEM can detect when attackers gain elevated access to systems or networks, by monitoring user activity and identifying unusual patterns of privilege escalation.
- Account hijacking: SIEM can detect when attackers take control of user accounts, by monitoring login activity and identifying unusual patterns of account access.
- Zero-day exploits: SIEM can detect zero-day exploits by analyzing network traffic and identifying suspicious behavior that may indicate an attempt to exploit a previously unknown vulnerability.
- DNS tunneling: SIEM can detect DNS tunneling, a technique used by attackers to exfiltrate data from networks by encoding it in DNS requests, by analyzing network traffic and identifying suspicious patterns of DNS requests.
- Man-in-the-middle (MitM) attacks: SIEM can detect MitM attacks, in which an attacker intercepts communication between two parties in order to eavesdrop or modify the content, by analyzing network traffic and identifying suspicious patterns of network activity.
- Insider threats: SIEM can detect insider threats, in which authorized users intentionally or unintentionally put the organization’s security at risk, by monitoring user activity and identifying unusual patterns of behavior.
- File integrity monitoring: SIEM can detect unauthorized changes to critical files, configurations, or system settings, by monitoring file integrity and alerting security teams to potential security incidents.
- Credential stuffing attacks: SIEM can detect credential stuffing attacks, in which attackers use lists of previously stolen usernames and passwords to try and gain unauthorized access to systems or applications, by monitoring login activity and identifying patterns of suspicious behavior.
- Malware infections: SIEM can detect when malware infects systems, by monitoring system and network activity and identifying suspicious patterns of behavior that may indicate the presence of malware.
- Denial of Service (DoS) attacks: SIEM can detect DoS attacks, in which attackers flood systems with traffic in order to disrupt service or bring them down, by analyzing network traffic and identifying patterns of suspicious behavior.
- Advanced malware: SIEM can detect advanced malware, which is designed to evade traditional security measures such as antivirus software, by analyzing network and system activity and identifying patterns of suspicious behavior.
- Supply chain attacks: SIEM can detect supply chain attacks, in which attackers compromise third-party software or hardware providers in order to gain access to target organizations, by monitoring network activity and identifying patterns of suspicious behavior.
- Malicious insiders: SIEM can detect malicious insiders, who are authorized users who intentionally act against the interests of the organization, by monitoring user activity and identifying unusual patterns of behavior.
- Fileless attacks: SIEM can detect fileless attacks, which are a type of malware attack that does not require a file to be written to disk, by monitoring system and network activity and identifying patterns of suspicious behavior.
- Cryptojacking attacks: SIEM can detect cryptojacking attacks, which involve the unauthorized use of a victim’s computer to mine cryptocurrency, by monitoring system and network activity and identifying patterns of suspicious behavior.
- These are just a few examples of attacks that can be detected by SIEM. SIEM can be used to detect many different types of attacks and is often an essential tool for detecting and closing security vulnerabilities in an organization.
- Now let me share sample scenarios to detect these attacks.
- Mail Masquerade Detection: Warn if an e-mail was received from e-mail addresses similar to the original e-mail address like: [email protected] and ali.veli@citibαnk.com
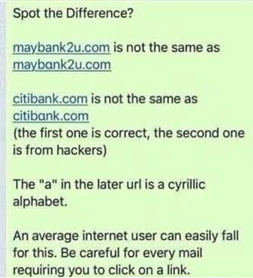
- Masquerading Detection: Detect system utilities, tasks, and services Masquerading. (T1036.003 Rename System Utilities Rename, T1036.004 Masquerade Task or Service)
- Abnormal auth behavior: the user has never authenticated to this machine before at this time
- Warn if a user is doing two different jobs at the same time (successful session-failed session, VPN-local login, URL Access-file Access, etc.)
- Abnormal auth behavior: the user has never authenticated to this machine before from this source machine
- Warn if a virus is detected on a client machine and not cleaned within 24 hours
- Warning if a user is doing the same job on different systems at the same time (database and local login, log in on two servers at the same time, downloading files from the internet, and running processes)
- Warn if the sum of the bytes processed parameter for web server access logs suddenly becomes too high
- Impossible travel detection
- If a user accesses sensitive files, and at the same time, the same user has a connection to file sharing sites, then notify.
- Warn if PowerShell command with base64 format and more than 100 characters appears
- Ratio of web errors is greater than %5
- Warn if a user makes three failed login attempts in 60 minutes without a successful login
- Warn if a server is shut down and not started within 24 hours
- Look for a user whose http to DNS protocol ratio is higher than %95 of the other users for the last four-week ratio for 4th day of week (today)
- The ratio of login success versus failure per user is an anomaly
- Multiple logons with the same credentials at the same time from different IPs
- Warn if a domain created in the last 24 hours is not in the top 1 million rankings and not in our whitelist
- Warn if Shannon entropy score of a filename or process name or domain name is higher than 7.2
- Hunting malware and viruses by detecting random strings
- Warn if a user’s VPN stays open for more than 4 hours
- Warn if a user created and not used for 72 hours
- Warn if the time between two login events of the same user is less than 1 minute
- Warn if the time between two logins failed events of the same user is less than 1 minute
- If there is a port usage, which is very rare (like under %3)
- Warn if a user has visited the malicious categories on the proxy at least once a day for a week. (Bot Networks, Uncategorized, Malware, Spyware, Dynamic DNS, Encrypted Upload)
- Warn if a user who has not had a VPN for at least 15 days (20,30,40…265 days) has remote interactive logon on more than one (1) workstation in a short time.
- File excluded from your antimalware scanner at the same time as code was executed via a custom script extension on your virtual machine.
- Realizing that Paula from Marketing is signed in from a mobile device and her office PC at the same time
- TeamViewer activity and the download of Notepad++ was taking place at the same time
- Warn if IP URL blocked by mail gateway is not blocked by Proxy.
- DGA detection
- If an account not used in at least the last 30 days (31,40,60,90,180 days etc ..), notify/lock/delete the account
- Entropy to detect randomness of HTTP host value: Identify suspicious requests by reviewing queries of domains with a high level of entropy.
- Calculate the randomness of PowerShell script contents that were executed.
- Same source ip, over 300,000 bytes message size within 1 minute to destination port 53
- New city access for the first time
- Abnormal auth behavior: the user has never authenticated to this machine before at this time
- VPN connection from a known anonymous proxy
- Suspicious creation of new network ACL
- Suspicious creation of security group
- Suspicious deleting a rule from a network ACL
- Suspicious deletion of customer gateway
- Abnormal number of discover requests from a client
- Abnormal activity duration/session count
- Abnormal number of bytes transmitted
- Abnormal amount of data egressed to competitor domains compared to past behavior
- Abnormal amount of data egressed to non-business domains compared to past behavior
- Abnormal amount of data egressed to personal email account compared to past behavior
- Abnormal amount of data egressed to removable media compared to past behavior
- Abnormal amount of login attempt detected on MFA
- Abnormal Email counts
- Abnormal session start time
- Access to internal applications / servers/ peers
- Account creation/ disable/ lockout / deletion rates
- Activity duration/ session counts
- Authentication anomaly-Country Mismatch
- Entropy Mismatch
- Excessive user logons on hosts
- First access to database MSSQL for user
- First access to device for the user
- First activity from ISP
- First connection from Source IP
- First time user is performing an activity from this device
- First VPN connection from device for the user
- High number of accounts from the same IP for authentication failures or lockout events
- High number of accounts from the same IP for successful authentications or run as events
- High number of accounts used on a workstation for authentication failures or lockout events
- High number of accounts used on a workstation for successful authentications or run as events
- High number of hosts accessed for authentication failures or lockout events
- High number of hosts accessed for successful authentication events or run as events
- High number of hosts accessed while enumerating critical ports
- High number of redirected/blocked attempts
- High number of run as activity across hosts
- High number of server errors
- If a user accesses sensitive files and at the same time the same user has a connection to file sharing sites then notify
- If an account not used in at least the last 30 days (31–40–60–90–180 days etc.) notify/lock/delete the account automatically
- Logon from a rare country
- New host logins
- New processes / Registry changes
- Odd time of access (first and last access)
- Odd time of email activity
- Odd time of logins
- Password change rates
- Successful/Failed login activity rates
- Upload/download deviations
- Warn if the sum of the bytes processed parameter for web server access logs suddenly becomes too high
- Login time to this machine is abnormal
- Warn if a user’s VPN stays open for more than 4 hours
- Warn if a user created and not used for 72 hours
- Warn if the time between two login events of the same user is less than 1 minute
- Warn if the time between two logins failed events of the same user is less than 1 minute
- If there is a port usage, which is very rare (like under %3)
- Warn if a user has visited the malicious categories on the proxy at least once a day for a week. (bot networks, uncategorized, malware, spyware, dynamic DNS, encrypted upload)
- Warn if a user who has not had a VPN for at least 15 days (20,30,40…265 days) has remote interactive logon on more than one (1) workstation in a short time.
- File excluded from your antimalware scanner at the same time as code was executed via a custom script extension on your virtual machine.
- Realizing that Paula from marketing is signed in from a mobile device and her office pc at the same time
- TeamViewer activity and the download of notepad++ was taking place at the same time
- Warn if IP/URL blocked by mail gateway is not blocked by proxy.
- This user has not logged in during this time spot before, which is abnormal.
- The number of login activities for this user within this time spot is abnormal.
- It is rare for this user to use this port.
- If there are more than 15,000 events from 50 unique IPs in 15 minutes, and these events fall under ten(10) unique categories, notify.
- If the ratio of failed login attempts to successful login attempts in the last hour exceeds 5%, notify.
- If a user’s total traffic in the last hour exceeds the 90th percentile of their total traffic usage in the last week by more than 10%, notify.
- If there is an abnormality in the number of alerts generated by the IPS (intrusion protection system) during this time zone by looking at historical data, notify.
- If a user accesses a domain they haven’t visited in the last day (or seven (7) days, or one (1) month), notify
- If the difference between a user’s total download traffic yesterday (or in the last seven (7) days or one (1) month) and their total download traffic today is more than 25%, detect it.
- If a new user logs in from a source IP to a target IP, detect it.
- If the hourly login failure or success authentication rate exceeds 3%, detect it.
- If the hourly HTTP/DNS rate is less than 1, detect it.
- Notify if a user connects to a VPN and logs in locally simultaneously.
- Notify whenever a user makes three unsuccessful login attempts consecutively within 30 minutes. (Without any successful login in between)
- Do not trigger an alarm if a user is erased within 10 minutes of creation if this user did not use it ever. But send out a warning if it is used and subsequently erased.
- If the same IP address logs in first to a Linux server and then to a Windows server, and then a service is opened/closed on one of these servers, generate an alert.
- If a user makes at least three unsuccessful login attempts within 10 minutes without any successful login attempts in between, generate an alert.
- If there has been no login for more than 3 months, generate an alert.
- Create an alert if a user is created and isn’t utilized for 72 hours.
- Provide an alert if a user log on to many workstations using remote interactive login after not using VPN for at least 15 days (20, 30, 40, or 365 days).
- Notify if several requests with requestMethod=POST are sent to multiple destination IP addresses within 5 minutes, and the port is higher than 1024, is not a well-known proxy target port, and has not been used for at least the last 30 days (20, 30, 40, or 365 days).
- If a machine or user who has been silent for at least 30 days (40 days, 60 days, 90 days, 365 days) is seen on the network again, shut down the machine and disable the user.
- Notify when a user logs into multiple workstations at the same time
- Alert when a user accesses a sensitive file or folder that they have not accessed before
- Notify when a user changes their password multiple times within a short period of time
- Notify when a user attempts to access a restricted website or service
- Notify when a user attempts to access a network resource from an unauthorized location or device
- Alert when a file with a known malware signature is detected on a workstation or server
- Notify when a user attempts to install software on their workstation without proper permissions
- Notify when a user attempts to bypass security measures, such as disabling antivirus software or accessing a blocked website using a proxy server.
- Abnormal number of files being created or modified by a user
- Abnormal number of failed logins from a particular IP address
- Abnormal amount of network traffic from a particular IP address or subnet
- Abnormal activity during non-business hours
- Abnormal activity in user accounts that have been inactive for a long time
- Abnormal activity on a user account that has been recently created
- Abnormal use of USB devices on a system
- Abnormal access patterns to sensitive data by a user
- Abnormal use of PowerShell commands or scripts
- Abnormal use of batch files or command line tools
- Abnormal use of remote access tools like RDP or SSH
- Abnormal use of mobile devices to access sensitive data or systems
- Abnormal use of web proxies or VPN services on a network
- Abnormal use of social media or file sharing services on a network
- Abnormal use of encryption tools like TrueCrypt or VeraCrypt
- Abnormal use of network protocols like SMB or FTP
- Abnormal use of file types or extensions not commonly used on a network
- Abnormal use of remote file transfer tools like SCP or SFTP
- Abnormal number of files being created or modified by a user
- Notify if a user downloads a large amount of data in a short period of time.
- Alert if a user tries to log in with a username or password that is known to be compromised.
- Notify if a user tries to access a resource they do not have permissions for, or if they try to escalate their privileges without authorization.
- Detect if a file or folder is being accessed or modified by an unauthorized user or process.
- Notify if a user is accessing a sensitive resource without using multi-factor authentication.
- Alert if a user attempts to execute a script or program that is known to be malicious.
- Detect if a device is connected to the network that is not authorized, or if a device is exhibiting unusual behavior.
- Notify if a user attempts to install unauthorized software on their device or on the network.
- Detect and notify multiple login attempts from different locations at the same time, which could indicate a brute-force attack on a user’s account.
- Monitor and alert network traffic for multiple connections from the same IP address at the same time, which could indicate a potential denial-of-service (DoS) attack.
- Identify and notify multiple instances of the same user account being active at the same time, which could indicate an account compromise or unauthorized access.
- Alert when a user attempts to access sensitive data or systems from multiple locations at the same time, which could indicate a potential data breach or insider threat.
- Monitor and alert access logs for multiple failed login attempts from the same user at the same time, which could indicate an attempted password-guessing attack.
- Alert when a user is logged in from multiple geographic locations simultaneously, indicating a possible account compromise or unauthorized access.
- Monitor and alert for multiple login attempts from the same IP address within a short period, which could indicate a brute-force attack.
- Detect and alert when multiple users are accessing the same sensitive file or database at the same time, indicating a potential breach of access controls.
- Identify and alert when a user is logged in from both a corporate network and a public Wi-Fi network at the same time, which could indicate a potential security risk.
- Notify when a user attempts to access multiple restricted resources simultaneously, suggesting an attempt to escalate privileges or bypass security controls.
- Alert when a user is accessing a critical system from multiple devices at the same time, suggesting a possible account compromise or data exfiltration.
- Detect and alert when multiple users are attempting to access a single resource at the same time, indicating a potential denial-of-service attack.





