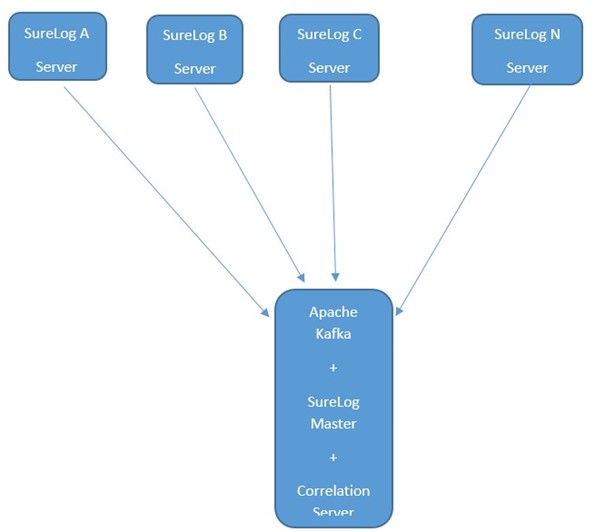
SureLog SIEM Blogs Central
Blog resources to illuminate the threat and siem logs. Browse our library of, solutions briefs, research reports, case studies, webinars and more.
Using a Security Information and Event Management (SIEM) System That Requires Dozens of Times Less Disk Space Than Market Leaders
Disk Costs Using a Security Information and Event Management (SIEM) system that requires dozens of...
Cyber Insurance and SIEM: Enhancing Security and Coverage
As the cybersecurity landscape continues to evolve, Security Information and Event Management (SIEM) solutions have...
SureLog SIEM’s Efficient Strategies for Keeping Logs Accessible (Hot) and Secure for Extended Duration with Minimal Disk Usage
SURELOG SIEM ACCESSIBLE (HOT) LOG RETENTION In the domain of data management and cybersecurity, maintaining...
Leveraging SureLog Big Data Infrastructure and AI Chatbot for Anomaly Detection
In today's swiftly evolving technological landscape, the proactive identification of anomalies within expansive datasets has...
Introducing SureLog: The Future of SIEM Solutions
In the rapidly evolving world of security information and event management (SIEM), SureLog stands out...
How Can LLMs Be Used in SIEMs?
Large Language Models (LLMs) like OpenAI's GPT can be integrated into Security Information and Event...
Advancing Cybersecurity with SureLog SIEM: Breaking EPS Boundaries, Leading in Efficiency, and Implementing Multi-Layer Detection Systems
In the ever-evolving landscape of cybersecurity, staying ahead of threats requires more than just reactive...
The Importance of Keeping Live Logs for Incident Response
There are many recommendations and regulations mandating long-term hot, online, immediately available, and live logs....
Hot, online, live logs: The Importance of Real-Time Log Data for SIEM
Hot, online, live logs are a critical component of any SIEM (Security Information and Event...
SURELOG SIEM PROFILER
SureLog leverage automated behavioral profiling to automatically detect anomalies and autonomously dfine rules on the...
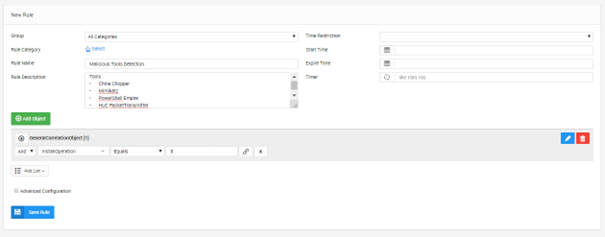
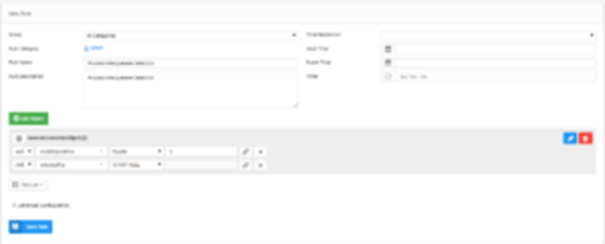
SureLog SIEM Sample Use Cases -Rules&Models
“Every Journey starts with a single step” A SIEM Security Use Case is this first...
GDPR Access Controls, Look at How You Manage Permissions.
GDPR requires organizations to gain explicit permission for any personal data use beyond the original...
SureLog SIEM User Behavior Monitoring Rules
Monitoring user behaviors with SureLog SIEM is easy and manageable. This article may interest you...
Anatomy of a Intrusion Detection Using SureLog SIEM
The primary benefit of a SIEM system to any organization, is the fact it immensely...
SureLog SIEM Taxonomy
How come SureLog detects things like a failed login from all brands and types of...
Why SureLog is the Right SIEM Solution?
1. Scalability — Ensure the solution has the capability to accommodate the current and the...
Detecting Unusual Activities Using a Next Generation SIEM -Use Cases Part 2
This article is part of a series. Check out the full series Part1 [1]. The...
Detecting Unusual Activities Using a Next Generation SIEM: Use Cases
Next-Gen SIEMs have brought new capabilities to organizations and their security teams. They’re built from...
Hot Data/Log in SureLog SIEM
Hot data is necessary for live security monitoring. Archive data is not available fastly. It...
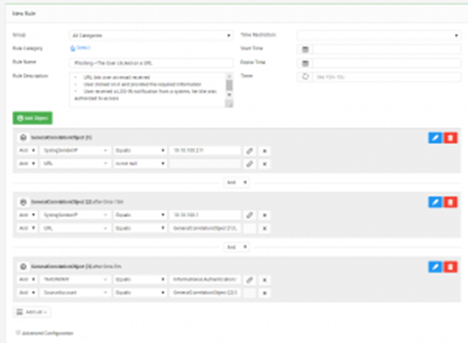
SureLog Correlation Engine and Beyond — Rule As a Code
SureLog SIEM is a security platform which differs from many SIEM products. The main difference...
Impossible Travel Detection in Real-TimeWith SureLog SIEM
You might need to detect when the same account is logged into twice in a...
SureLog SIEM “At The Same Time” Operator
Correlation is a must for SIEM solutions. But, the detection capabilities of the SIEM products...
DETECTING RANSOMWARE ATTACKS WITH SURELOG SIEM
Ransomware is a top security concern for organizations today. Malicious actors continue to develop new...
SURELOG LISTS
Lists are available in most (if not all) SIEMs. Lists are different in each of...
DNS Log Analysis for Network Security in SureLog SIEM
DNS has an important role in how end users in your enterprise connect to the...
Detecting A User Logged Via LAN and Simultaneously Connected to VPN by Designing a Rule with SureLog SIEM
Scenario: This correlation scenario enables the detection of abnormal events in remote connection sessions that...
History and Evaluation of SIEM Correlations
The Battle of Agincourt. Chroniques d’Enguerrand de Monstrelet (early 15th century)/Wikimedia Commons/Public DomainThis article may...
Hot, online, live logs: The Importance of Real-Time Log Data for SIEM
This article may interest you SQL Streaming Based Thread Detection in SureLog SIEM Hot,...
SQL Streaming Based Thread Detection in SureLog SIEM
In the realm of cybersecurity, threat detection is of utmost importance to protect organizations from...
The Importance of Keeping Live Logs for Incident Response
There are many recommendations and regulations mandating long-term hot, online, immediately available, and live logs....
Is SIEM really dead? Does XDR or other Technologies replace SIEM? What Types of Attacks Does SIEM Detect?
The world of cybersecurity is constantly evolving and the need for advanced security measures has...
Detecting Unusual Activities Using SureLog Next Generation SIEM: Use Cases
Next-Gen SIEMs have brought new capabilities to organizations and their security teams. They’re built from...
DETECTING TOP 4 TOOLS USED BY CYBER CRIMINALS RECENTLY WITH SURELOG
Cyber Criminals are using various malicious tools for cyber-attacks based on the target’s strength to...
Creating New Dashboards With SureLog SIEM
The SureLog application features dashboards on various security topics. Dashboards deliver monitoring and reporting metrics...
Anomaly Detection with SureLog SIEM UEBA Module Using RPCA
Anomaly detection in sequence data is becoming more and more important to detect intrusions in...
Anomaly Detection with SureLog SIEM UEBA Module Using Markov Chain
Anomaly detection in sequence data is becoming more and more important to detect cyber security...
VPN Security Monitoring SureLog SIEM Use Cases
• Monitor VPN connection from an anonymous proxy o Monitor connection to VPN providers and...
User and Entity Profiling with SureLog
Organizations need to guard against not only outsider cyber criminals but also rogue insiders. To...
Threat Detection and Hunting with MITRE ATT&CK Techniques Using SureLog SIEM
Spearphishing Link (T1192) Spearphishing with a link is a specific variant of spearphishing. It is...
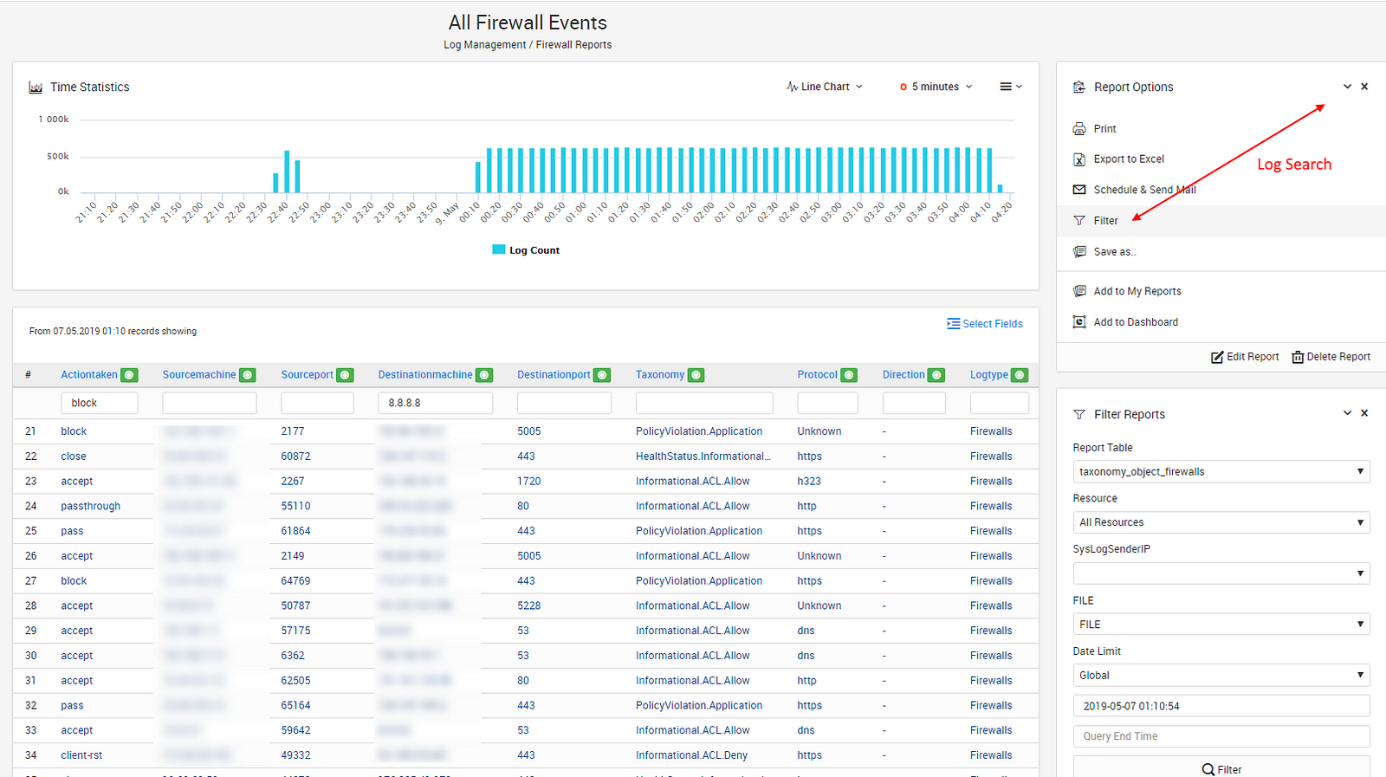
The Fastest Way to See What is Going on Your Network’s Security Aspect is SureLog SIEM
With SureLog SIEM it is possible to see what happened by looking at a picture...
SURELOG TAXONOMY
A taxonomy improves the scope and stability of correlation rules. It also aids in pattern...
SureLog SIEM Use Cases
Not all security information and event management (SIEM) use cases are equally important. The most...
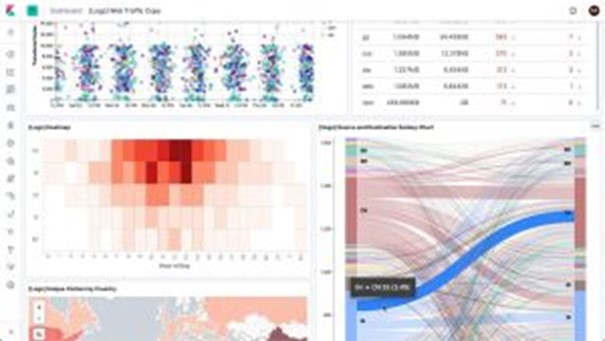
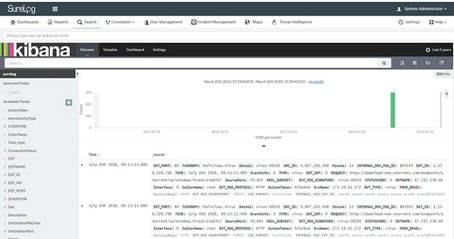
SureLog SIEM Security Data Visualization Enrichment With Kibana
SureLog recently integrated with Kibana, an open-source data visualization tool that provides additional flexibility when...
SURELOG SIEM HAS MOST VALUABLE SIEM USE CASES
SureLog Rule As a Code [1] streaming platform detection capability is more than traditional SIEM...
SureLog SIEM Federated Anomaly Detection Engine Using Classification
Next generation detection engine of SureLog SIEM combining rule based and ML based techniques. SureLog...
SURELOG SIEM AND ADVANCED THREAT ANALYTICS WITH MACHINE LEARNING (ML)
SureLog SIEM comes with advanced correlation engine, behavioral analytics and Machine Learning (ML) models to...
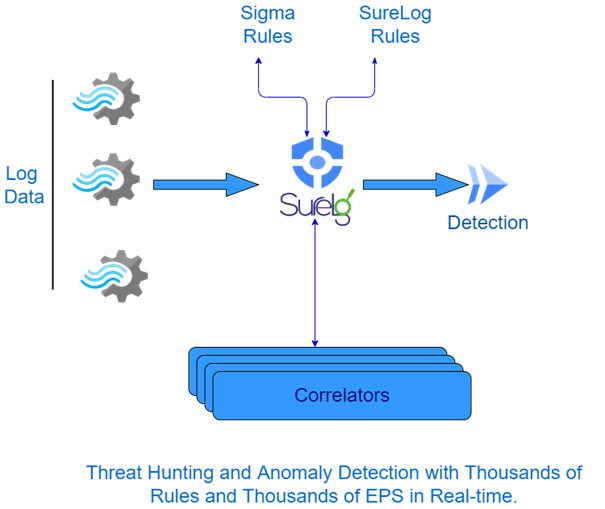
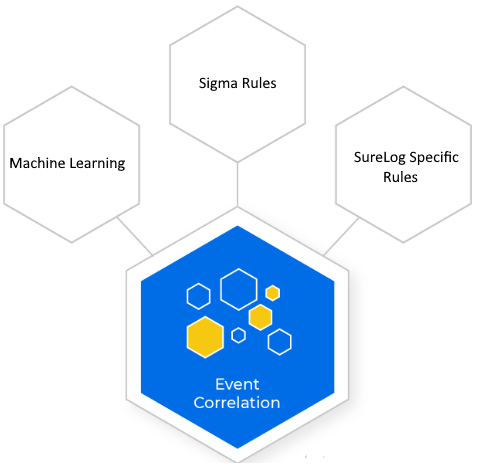
Real Time Sigma Rules & SureLog Correlation Engine
As we know SIEM solutions are critical needs for cyber security and also for SOC....
Real Time Multi-Dimensional Data and Log Enrichment with SureLog SIEM
Data enrichment is the key ingredient required for effective threat detection, investigation, and response. Using...
Not All SIEM Solutions Are Equal and Not All SIEM Use Cases Are the Same
Security Information and Event Management (SIEM) solutions are an important tool in a modern day...
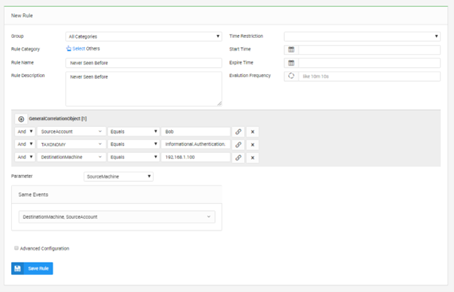
Never Seen Before Type of Rules With SureLog SIEM
Event correlation techniques are designed to detect events, make sense of them and assign the...
Malware Fighting with SureLog SIEM
We will show you how SureLog SIEM can effectively identify and stop malware on the...
Log Storage and Hot Data
Hot data necessary for live security monitoring and cold data is for which you may...
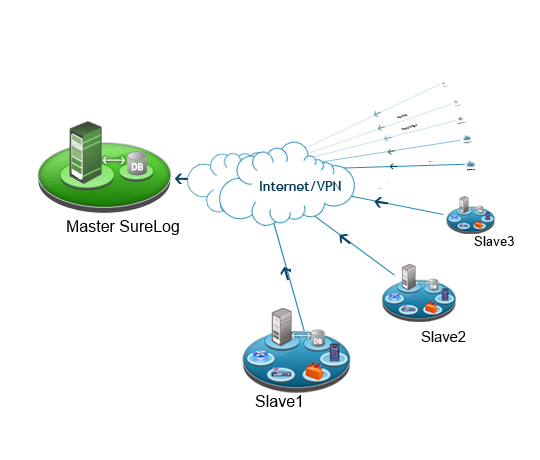
Large Scale SureLog SIEM Implementation
Today’s computer networks produce a huge amount of security log data. The security event correlation...
Implementing Windows Advanced Logging Cheat Sheet with SureLog SIEM
There are many references to Windows Advanced logging. [1] [2]. Windows has some great built-in capabilities...
Hunting Malware and Viruses by Detecting Random Strings Using SureLog SIEM
There are malware tools available that can create Windows services with random service names and...
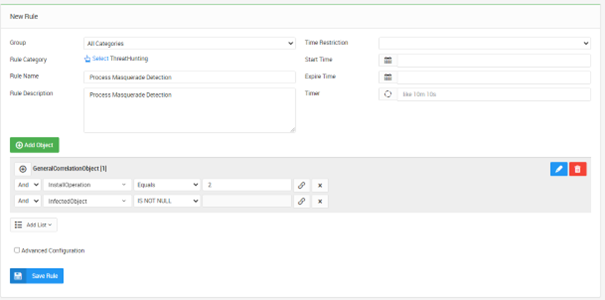
Hunting Critical Process Masquerade Using SureLog SIEM
A popular technique for hiding malware running on operating systems is to give it a...
How to Search Billions of Logs Without learning New Script Language With SureLog SIEM?
SureLog is a solution that allows you to build your own search logic without a...
GDPR Use Cases
A SIEM’s power is in its correlation. SureLog has advanced threat detection capabilities. SureLog combines...
Domain Generation Algorithm (DGA) Detection in SureLog
DNS is probably the best source of data for detecting an attacker’s command and control...
The True Power of SureLog Taxonomy
SureLog standardizes the category of activities collected from log and machine data. SureLog has a...
Surelog siem and advanced threat analytics with machine learning
SureLog SIEM comes with advanced correlation engine, behavioral analytics and Machine Learning (ML) models to...
How to spot and stop malware?
Organizations still get hit with malware and ransomware in spite of that fact that antivirus...