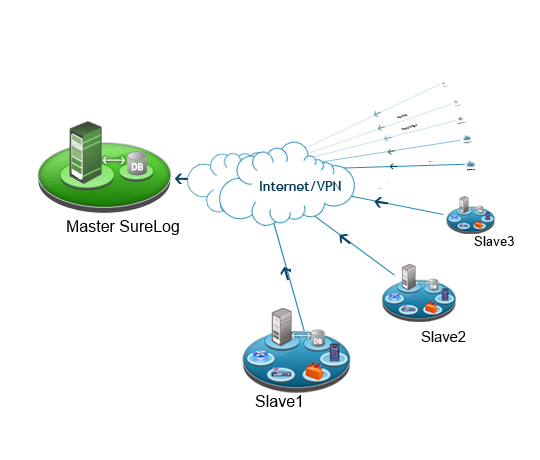
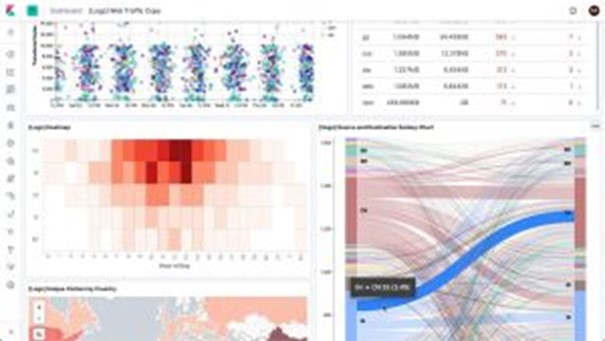
In the ever-evolving landscape of cybersecurity, staying ahead of threats requires more than just reactive measures—it demands innovation, efficiency, and a comprehensive approach to threat detection. In this article, we’ll explore how cutting-edge SIEM (Security Information and Event Management) solutions are breaking boundaries, leading in efficiency, and implementing multi-layer detection systems to elevate security standards.
🔒 Breaking EPS Boundaries
Traditional SIEM solutions often struggle to keep pace with the exponential growth of data generated by modern digital environments. However, innovative SIEM platforms are breaking EPS boundaries by redefining how they handle Event Per Second (EPS) data. By leveraging advanced algorithms, distributed processing, and scalable architectures, these solutions can effectively process massive volumes of data in real-time, enabling organizations to detect and respond to threats swiftly.
Breaking EPS boundaries not only enhances the scalability and performance of SIEM systems but also empowers organizations to gain deeper insights into their security posture by analyzing a broader spectrum of data sources. SureLog SIEM is the only solution that guarantees compatibility with the SANS EPS calculation table.
🔥 World Leader in Efficiency
Efficiency is paramount in cybersecurity operations, where every second counts in detecting and mitigating threats. Leading SIEM solutions are setting new standards in efficiency by optimizing resource utilization and streamlining operations.
One key area where efficiency shines is in log management. By implementing intelligent data compression techniques and advanced storage optimization algorithms, SIEM platforms can significantly reduce the storage footprint, leading to 10 to 40 times less hot log disk usage. SureLog SIEM requires less than 10 TB of disk space to retain logs for one year at a rate of 10,000 EPS. This not only conserves valuable storage space but also enhances overall system performance and reduces operational costs.
Efficiency extends beyond storage optimization—it encompasses the entire SIEM workflow, from data collection and normalization to correlation and analysis. By automating routine tasks, eliminating false positives, and prioritizing alerts based on risk levels, efficient SIEM solutions empower security teams to focus their efforts where they matter most. SureLog SIEM keeps logs hot for a year without additional disk space.
🛡️ Multi-Layer Detection System
In today’s threat landscape, adversaries are becoming increasingly sophisticated, employing diverse tactics to evade detection. To combat this evolving threat landscape, modern SIEM solutions deploy a multi-layer detection system that combines multiple detection methods and techniques.
This multi-layer approach to threat detection enables SIEM platforms to cast a wider net, detecting a broader range of threats across different attack vectors. From signature-based detection and behavioral analytics to anomaly detection and threat intelligence integration, each layer contributes to a comprehensive defense posture that is resilient against both known and emerging threats.
Deploying a multi-layer detection system is essential since no single detection method can find all threats. This includes CEP Based (Real Time), Real-Time Sigma Rules, SQL Streaming Based Rules, Behavior Analysis, Anomaly Detection (Outliers), Comparative Correlation (comparing last hour activity with last day/week/month activity), and the Industry First: Detection (Rule) as Code since 2018 (source: ResearchGate) using Java, Mvel, and Python.
Furthermore, the integration of machine learning and artificial intelligence enhances the efficacy of the multi-layer detection system by continuously learning from past incidents and adapting to evolving threats in real-time.
In conclusion, breaking EPS boundaries, leading in efficiency, and implementing a multi-layer detection system are crucial pillars of modern SIEM solutions. By embracing innovation and leveraging these advancements, organizations can strengthen their security posture, mitigate risks effectively, and stay one step ahead of cyber threats.
Stay tuned for more insights on cybersecurity trends and best practices. If you’re interested in learning how our SIEM experts can help secure your organization, reach out to us today. Your security is our priority.