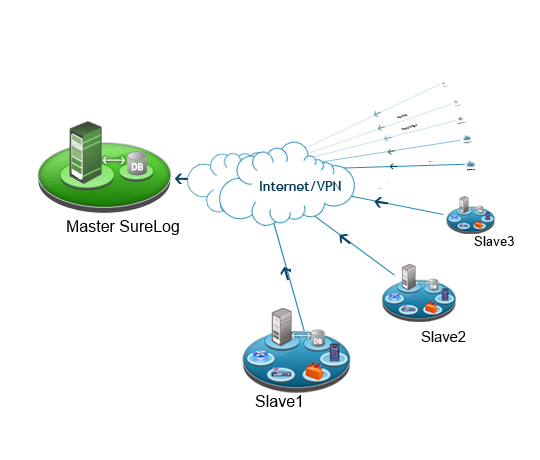
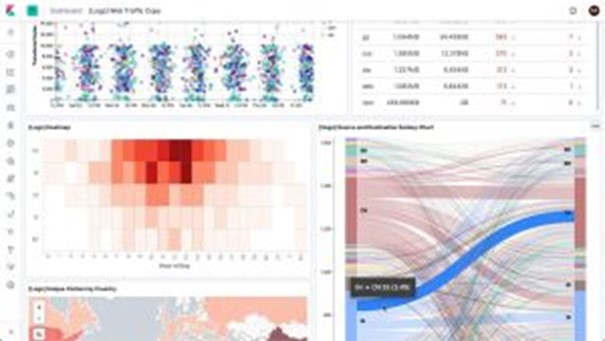
Large Language Models (LLMs) like OpenAI’s GPT can be integrated into Security Information and Event Management (SIEM) systems to significantly enhance their capabilities in several ways. The integration of LLMs can transform SIEMs from traditional security monitoring tools into advanced, intelligent platforms capable of providing deeper insights, automating complex processes, and improving the overall efficiency of security operations. Here’s how LLMs can be utilized in SIEMs:
Automated Log Analysis
LLMs can automatically analyze vast volumes of logs to identify patterns, anomalies, or signs of cyber threats that might be overlooked by traditional methods. By understanding the context within logs, LLMs can reduce false positives and highlight genuine security incidents, thereby improving the accuracy of threat detection.
Natural Language Queries
LLMs enable users to interact with SIEM systems using natural language queries, making it easier for security analysts to extract specific information from complex datasets. Analysts can ask questions in plain English, and the LLM can interpret these queries to provide relevant information, simplifying data analysis and speeding up incident response.
Threat Intelligence Generation
By analyzing current and historical security data, LLMs can generate actionable threat intelligence, offering insights into potential vulnerabilities, attack patterns, and recommended countermeasures. This capability can help organizations proactively address security weaknesses before they are exploited.
Incident Response Automation
LLMs can automate parts of the incident response process by generating scripts or workflows based on the specific characteristics of a detected threat. For instance, if a SIEM detects a phishing attempt, the LLM could automatically draft communication to the IT department or affected users, advising them of the threat and suggesting preventive measures.
Enhanced Reporting and Documentation
LLMs can assist in generating detailed security reports, audits, and compliance documentation by summarizing key data points and findings from the SIEM. This can save time for security teams and ensure that reports are comprehensive and easily understandable.
User and Entity Behavior Analysis (UEBA)
Integrating LLMs with UEBA features in SIEMs can improve the detection of insider threats, compromised accounts, and lateral movement within a network. LLMs can analyze behavior patterns to distinguish between legitimate activities and potential security threats, enhancing the precision of behavioral analytics.
Security Training and Awareness
LLMs can be used to create customized security training programs and simulations based on the specific threats and vulnerabilities an organization faces. By analyzing past incidents and current trends, LLMs can help design training scenarios that are both relevant and effective in improving security awareness among employees.
Security Orchestration, Automation, and Response (SOAR)
LLMs can contribute to the automation of response actions by providing decision support, generating scripts, or automating communications with other security tools within the SOAR framework.
Reducing False Positives
Through more sophisticated analysis and understanding of context, LLMs can help reduce the number of false positives generated by SIEM systems, allowing security teams to focus on genuine threats.
Enhanced User Interaction
LLMs can improve the interface between SIEM systems and security analysts through natural language queries and explanations, making it easier for analysts to interact with the system and extract meaningful information.
Chatbots for Security Operations
LLMs can power chatbots that provide 24/7 assistance to security teams, offering quick access to information, guidance on incident resolution, and support for routine tasks. These chatbots can improve operational efficiency and help security analysts focus on more strategic activities.
Integrating LLMs into SIEM systems represents a significant leap forward in making cybersecurity operations more intelligent, efficient, and proactive. However, it’s important to manage the integration thoughtfully, considering the security and privacy implications of using LLMs, especially in handling sensitive data and ensuring that the AI’s recommendations are validated by experienced security professionals.
Exploring Some Well-Known Commercial and Open-Source LLMs
As we are introducing the usefulness of LLMs in the field of SIEM, understanding the landscape of available models becomes significant. Let’s spotlight notable LLMs – GPT-3 , BERT , Microsoft’s Turing Models, GPT-Neo and GPT-J by Eleuth, Hugging Face’s Transformers Library, XLNet , RoBERTa , Mixtral 8x7B, Vicuna, Falcon, and WizardLM – each contributing uniquely to the diverse applications which can be useful in SIEM practices.
Commercial LLMs
GPT (Generative Pretrained Transformer) Series by OpenAI
GPT-3 and its successors (such as GPT-4) are among the most powerful and widely recognized commercial LLMs. They are known for their ability to generate human-like text, perform language translation, generate creative content, and more. OpenAI offers these models through a paid API, which is used by businesses and developers to integrate advanced language capabilities into their applications.
BERT (Bidirectional Encoder Representations from Transformers) by Google
BERT is another influential model primarily used to understand the context of words in search queries. While BERT itself is open-source, Google has leveraged it to significantly improve the understanding of search queries in its commercial search engine, making it a cornerstone of Google’s search technology.
Microsoft’s Turing Models
Microsoft has developed its own series of large language models known as Turing models, which are utilized across its range of products and services, including Bing, Office, and LinkedIn, to enhance search, grammar suggestions, and other AI-driven features.
Open-Source LLMs
GPT-Neo and GPT-J by EleutherAI
EleutherAI is a grassroots collection of researchers pushing the boundaries of open-source AI. GPT-Neo and GPT-J are their attempts to replicate the capabilities of GPT-3, offering powerful language models that the public can use and modify. These models aim to democratize access to cutting-edge AI technology.
Hugging Face’s Transformers Library
While not a model in itself, Hugging Face’s Transformers library is a comprehensive resource that provides easy access to a wide variety of both commercial and open-source pre-trained language models, including BERT, GPT-2, and RoBERTa. It facilitates the use, fine-tuning, and deployment of these models in various applications.
XLNet
XLNet is an open-source model developed by Google Brain and Carnegie Mellon University. It improves upon BERT by removing the pre-training and fine-tuning discrepancy by training the model on all permutations of the input data.
RoBERTa (A Robustly Optimized BERT Pretraining Approach) by Facebook AI
RoBERTa builds upon BERT’s language understanding capabilities with optimized training strategies, yielding more accurate models. While developed by Facebook AI, RoBERTa is available as an open-source model, making it widely accessible for research and application development.
Mixtral 8x7B
Mistral AI’s Mixtral 8x7B stands as a revolutionary open-weight model surpassing GPT-3.5 performance. Its Mixture of Experts (MoE) architecture ensures exceptional speed, making it suitable for chatbot use-cases when run on 2x A100s. With approximately 56 billion parameters, Mixtral adeptly handles a 32k token context, supports multiple languages, and excels in code generation. Finetuning transforms it into an instruction-following model with a notable MT-Bench score of 8.3.
Vicuna
Vicuna, an open-source chatbot by LMSYS (Large Model Systems Organization – an organization that develops large models and systems that are openly accessible, and scalable), fuses together the strengths of LLaMA and Alpaca. Derived from 125K user conversations, it achieves an impressive 90% ChatGPT quality, matching GPT-4. Tailored for researchers and hobbyists, Vicuna comes in two sizes—7 billion and 13 billion parameters. While akin to “GPT-3.25,” it outperforms GPT-3 in power and effectiveness, backed by the robustness of LLaMA.
Falcon
Developed by the Technology Innovation Institute, the Falcon LLM redefines AI language processing. With models like Falcon-40B and Falcon-7B, it delivers innovative capabilities for diverse applications. Trained on RefinedWeb, the open-source Falcon LLM features multi-query attention, ensuring scalability. Its Apache 2.0 license encourages widespread usage, setting it apart with custom tooling and enhancements like rotary positional embeddings and multi-query attention.
WizardLM
WizardLM distinguishes itself in tests against GPT-4 in 24 skills, outperforming even in technical domains and skills like academic writing, chemistry, and physics. This project focuses on enhancing LLMs by utilizing AI-evolved instructions for training, providing a practical option for more challenging tasks. While not claiming absolute superiority over ChatGPT, WizardLM’s preference in certain scenarios suggests the potential of AI-evolved instructions in advancing LLMs.
Differences Between Commercial and Open-Source LLMs
Access and Cost: Commercial models often require payment to access their APIs or services, while open-source models can be freely used, modified, and distributed.
Customization: Open-source models offer greater flexibility for customization and fine-tuning to specific needs or datasets.
Support and Maintenance: Commercial models typically come with professional support and regular updates, whereas open-source models rely on the community for development and maintenance.
Both commercial and open-source LLMs have their advantages and play crucial roles in the advancement of AI and natural language processing technologies. The choice between them depends on the specific needs, resources, and objectives of the users or organizations.
How to Fine-Tune LLMs to Use in SIEMs
Fine-tuning Large Language Models (LLMs) for use in Security Information and Event Management (SIEM) systems involves adapting the model to understand and process cybersecurity-related data effectively. This process allows the LLM to generate insights, detect anomalies, and provide recommendations based on the vast amounts of data processed by SIEM systems. Here’s a step-by-step guide on how to fine-tune LLMs for this purpose:
1. Define Objectives and Requirements
– Objective Definition: Clearly define what you want the LLM to achieve within your SIEM. This could range from detecting specific types of threats, generating alerts based on unusual activity, or automating responses to common incidents.
– Requirements Gathering: Understand the types of data your SIEM collects and what outputs are expected from the LLM. This could involve processing logs, network traffic data, or alerts from other security tools.
2. Data Preparation
– Dataset Collection: Gather a dataset that is representative of the security events and logs the SIEM handles. This dataset should include both normal operations and various types of security incidents.
– Data Labeling: Label your data accurately. For anomaly detection, label data as normal or malicious. For classification tasks, label the types of attacks or security events.
– Data Cleaning and Preprocessing: Cleanse the data to remove any irrelevant information. Format the data consistently, ensuring it’s suitable for training the model.
3. Model Selection
– Choose a Base Model: Select an LLM as your base model. Models like GPT-3, BERT, or open-source alternatives like GPT-Neo can serve as a starting point.
– Assess Model Suitability: Ensure the chosen model’s architecture and capabilities align with your SIEM’s requirements. Consider factors like processing power, response time, and the complexity of the data.
4. Fine-Tuning Process
– Custom Training Data: Use your prepared dataset to fine-tune the model. This step involves training the model to understand and generate responses based on the cybersecurity context of your data.
– Hyperparameter Tuning: Adjust hyperparameters such as learning rate, batch size, and the number of training epochs to optimize performance.
– Validation and Testing: Regularly validate the model on a separate portion of the dataset to monitor its performance. Adjust the training process based on these results.
5. Integration into SIEM
– API Development: Develop an API or interface to integrate the fine-tuned model with your SIEM system. This interface should allow the SIEM to send data to the model and receive its outputs.
– Workflow Integration: Define how the model’s insights are used within the SIEM workflow. This could involve automating certain responses, enriching alerts with additional information, or providing recommendations for analysts.
6. Continuous Improvement and Monitoring
– Performance Monitoring: Continuously monitor the model’s performance to ensure it meets the expected standards. This includes tracking false positives and negatives, response times, and accuracy.
– Model Updates: Regularly update the model with new data to ensure it remains effective as new types of threats emerge. This may involve periodic re-training or fine-tuning with updated datasets.
Best Practices and Considerations
– Ethical and Privacy Concerns: Ensure that the training and application of LLMs in your SIEM respect privacy laws and ethical guidelines, especially when handling sensitive data.
– Security of the Model: Protect the model from adversarial attacks that could manipulate its outputs or compromise its integrity.
– Scalability: Ensure that the integration of LLMs into your SIEM can scale with the volume of data and the complexity of security events it needs to process.
Fine-tuning LLMs for SIEMs is a complex but rewarding process that can significantly enhance the capabilities of security operations. By following these steps and maintaining a focus on continuous improvement, organizations can leverage the power of AI to bolster their cybersecurity efforts.