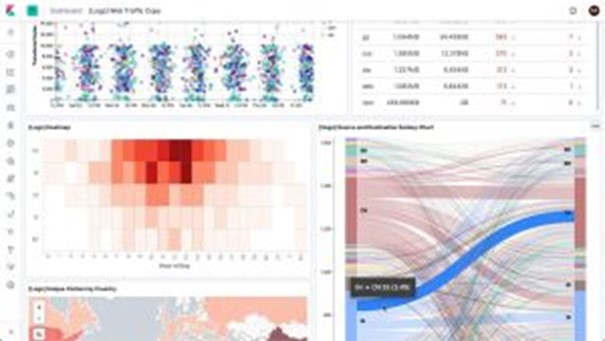
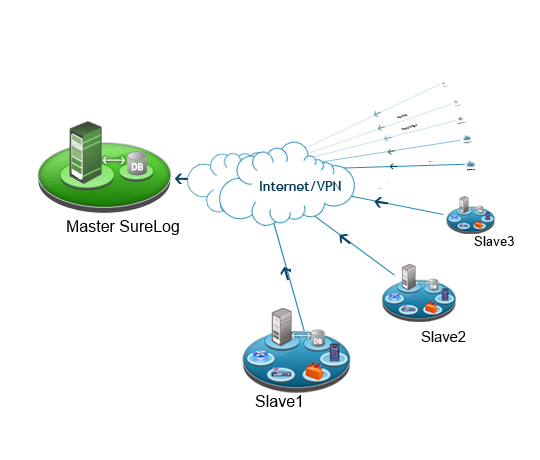
Hot, online, live logs are a critical component of any SIEM (Security Information and Event Management) system. These logs are continuously generated and readily accessible in real time, providing security teams with a valuable window into the activities taking place on their networks.
There are many benefits to using hot, online, live logs for SIEM. Here are some of the most important:
1. Real-time threat detection and response: Hot logs can be used to detect security events and incidents as they happen, allowing for immediate response and mitigation actions. This is in contrast to traditional log data, which is often stored in a centralized repository and can take hours or even days to be analyzed.
2. Early warning signs: Monitoring hot logs provides valuable insights into the early warning signs of potential security breaches. By analyzing log data in real time, security analysts can identify suspicious activities, patterns, or anomalies that may indicate a security incident in progress or an attempted attack. Detecting these warning signs early allows for faster incident response and proactive measures to mitigate the risk.
3. Forensic investigations: Hot logs are essential for post-incident forensic investigations. They provide a detailed chronological record of events, allowing security analysts to reconstruct the sequence of activities leading up to a security incident. Online access to these logs ensures that investigators can quickly analyze the data and identify the root cause of the incident, the extent of the breach, and any potential data exfiltration.
4. Compliance and auditing: Many industries and organizations have regulatory compliance requirements that mandate the collection and retention of logs for a specified duration. Hot, online, live logs ensure that organizations can meet these compliance requirements by capturing and storing logs in real time. This availability allows auditors and compliance teams to review logs promptly, ensuring adherence to security policies, regulations, and standards.
5. Incident response and threat hunting: Hot logs are valuable for incident response and proactive threat hunting activities. By monitoring live logs, security teams can proactively search for indicators of compromise (IOCs) or suspicious patterns that may signify an ongoing attack. This proactive approach enables security professionals to identify threats early, investigate potential security incidents, and take appropriate actions to contain and remediate the threats.
6. Incident timeline reconstruction: Hot logs can be used to reconstruct the timeline of events leading up to and during an incident. This is a critical aspect of incident response, as it allows security teams to understand how the attack unfolded and identify any gaps in their security posture. By analyzing hot logs, security teams can piece together the sequence of events, identify any lateral movement by the attacker, and assess the impact on systems and data.
7. Root cause analysis: Hot logs can also be used to perform root cause analysis of security incidents. By analyzing the logs in detail, security teams can identify the underlying factors that contributed to the breach. This information can then be used to improve security policies and procedures, reduce the risk of future attacks, and improve the overall security posture of the organization.
8. Proactive risk management: By monitoring hot logs, security teams can identify potential risks before they become incidents. This allows organizations to take proactive steps to mitigate these risks, such as implementing additional security controls or training employees on security best practices.
In addition to these benefits, hot, online, live logs also offer a number of other advantages, including increased visibility, improved efficiency, and enhanced decision-making.
However, the volume of hot logs can be significant, which can pose a challenge for organizations. To address this challenge, organizations can leverage SIEM solutions that utilize disk compression techniques to reduce the size of log files without sacrificing their integrity. These solutions allow organizations to store more logs for longer periods of time without worrying about running out of disk space. For example, a successful implementation of disk compression could handle up to 10,000 events per second (EPS) and store logs for 10 terabytes (TB) over the course of one year.
In summary, hot, online, live logs provide real-time visibility and insights into security events and incidents. They facilitate early threat detection, forensic investigations, compliance adherence, incident response, root cause analysis, and proactive risk management. While log volume can be a challenge, implementing solutions that leverage disk compression can help organizations effectively manage and store their log data. By utilizing hot, online, live logs effectively, organizations can enhance their security posture, meet regulatory requirements, and protect their data from potential threats.
SureLog is the SIEM solution that keeps logs live for the longest time using the least disk size in the world. SureLog uses 80–100 times less disk than competitors. 2.5 TB is enough to keep it alive for 12 months under a maximum of 3000 EPS log flow.