Ransomware is a top security concern for organizations today. Malicious actors continue to develop new techniques and strategies to trick victims into downloading and installing ransomware on victim their systems.
This article may interest you SQL Streaming Based Thread Detection in SureLog SIEM
Ransomware is a type of malicious software used by cybercriminals to encrypt a user or organization’s digital data (e.g., files, applications, databases) to block access until a ransom demand is met, generally in the form of a cryptocurrency payment. An extension of this act is double extortion ransomware, whereas adversaries not only demand payment in exchange for access, but also include an additional demand to prevent them from publishing sensitive data.

Ransomware Tactics and Deployment Techniques
Ransomware incidents have increased dramatically in the past few years. The number of ransomware variants is also increasing. Therefore, in order to combat ransomware, we need a better understanding on how ransomware is being deployed. Some of the more common means for distributing ransomware include the following:
Deployment Technique
Email Phishing: Email recipients are tricked into clicking on a malicious link or opening a file attachment that contains malware.
Social Media: Legitimate looking links located on common social media sites/applications that redirect to malicious websites.
Malvertising: Fake advertisements displayed on websites that redirect victims to malicious websites.
Drive-By Downloads: Malware in the form of viruses, keyloggers, trojans, and remote access tools that is unintentially dowloaded.
Removable Media: Storage devices, such as USB flash drives, containing malicious software that can spread to other devices/systems by unsuspecting users who connect them to their systems.
Remote Desktop Protocol (RDP): RDP client software is used to gain remote access to systems with privilege escalations and then used to access additional systems/networks.

Ransomware Detection Techniques
- New Processes and Software Execution: The launch of new processes and unrecognized programs can indicate the execution of malware dropped on a system. In this case, two logs have been identified with one from Microsoft Security Audit, Event ID 4688, and the other from Microsoft Sysmon, Event ID 1. Both logs are observing a Process Start event. SureLog SIEM uses its inbuilt alert rules to identify new processes and software execution.
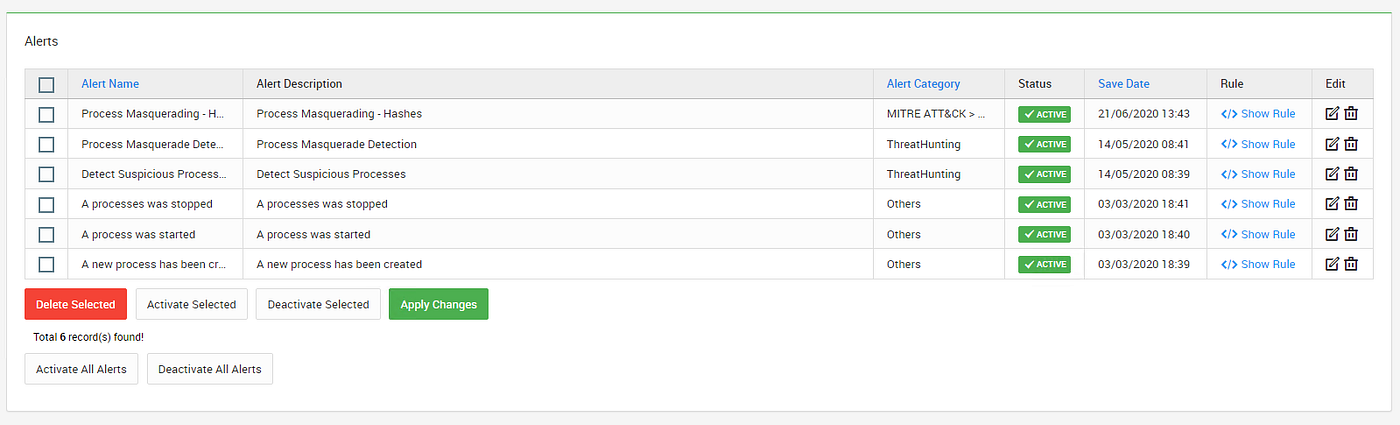
- Endpoint IoCs: Malware present on the system can be identified based on the changes it makes to the Windows registry, unusual parent/child process combinations and other endpoint indicators of compromise (IoCs). SureLog utilizes two Event IDs:
4663 — An attempt was made to access an object. This Event ID will not provide much security value for registry keys and can be filtered out of your log management solution for ONLY registry items (Task Category = Registry or Object Name = “\REGISTRY\*”). This Event ID is needed for file auditing, so do not filter out for file and folder items.
4657 — A registry value was modified. This is the primary Event ID that you want to focus in your registry auditing investigations on as they contain the key, value, data added or changed and the process that made the change providing the details most needed for registry monitoring.
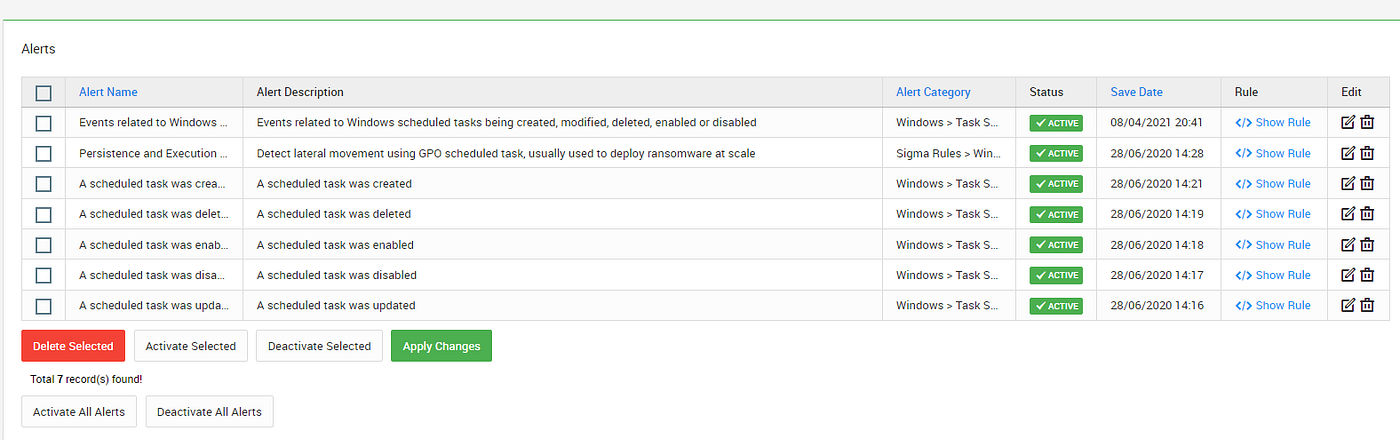
- Scheduled Task/Job: Adversaries may abuse task scheduling functionality to facilitate initial or recurring execution of malicious code. Utilities exist within all major operating systems to schedule programs or scripts to be executed at a specified date and time. A task can also be scheduled on a remote system, provided the proper authentication is met (ex: RPC and file and printer sharing in Windows environments). A scheduling a task on a remote system typically requires being a member of an admin or otherwise privileged group on the remote system. Adversaries may use task scheduling to execute programs at system startup or on a scheduled basis for persistence. These mechanisms can also be abused to run a process under the context of a specified account (such as one with elevated permissions/privileges). Related Event IDs
Event ID 106 on Windows 7, Server 2008 R2 — Scheduled task registered
Event ID 140 on Windows 7, Server 2008 R2 / 4702 on Windows 10, Server 2016 — Scheduled task updated
Event ID 141 on Windows 7, Server 2008 R2 / 4699 on Windows 10, Server 2016 — Scheduled task deleted
Event ID 4698 on Windows 10, Server 2016 — Scheduled task created
Event ID 4700 on Windows 10, Server 2016 — Scheduled task enabled
Event ID 4701 on Windows 10, Server 2016 — Scheduled task disabled
- Command and Control Traffic: Command-and-control (C&C) servers are the machines attackers use to maintain communication with the compromised systems in a target network. Using Threat Intelligence to Detect C&C Traffic is a common SIEM use case. SureLog SIEM may associate the network traffic with Threat Intelligence Module to discover malware that communicates with external attackers.
- Unusual System-to-System Connections: Ransomware and other malware usually try to spread laterally through the network to maximize its impact. Look for communications between systems that do not normally talk to one another. SureLog SIEM detects unusual or first seen type of activities. Example rule:
https://www.surelogsiem.com/2020/01/18/never-seen-before-type-of-rules-with-surelog-siem
- Elevated use of PowerShell: Many ransomware groups leverage PowerShell to propagate malware throughout a network. PowerShell loging can be used to detect such activities.
- Log Source Type MS Windows Event Logging — PowerShell: VMID 800 (if PowerShell is used in conjunction with a scheduled task)
o Log Source Type MS Windows Event Logging XML — Security: VMID 4688 and Log Source Type MS Windows Event Logging XML — Sysmon: VMID 1 (if a process, such as CMD, is involved with a scheduled task)
· Pass-the-Hash Indicators: Pass-the-Hash is an attack commonly used to expand an attacker’s access to a network. Pass-the-Hash traffic on the network points to an ongoing attack. Based on a Stealthebits blog, the simplest way to build detections for pass the hash is to look for:
4624 events on your workstations
Logon Type = 9
Authentication Package = Negotiate
Logon Process = seclogo
Associated Sysmon 10 events for LSASS process access
With a custom event correlation you can easily catch when these two things happen at the same exact time, you’ve got pass-the-hash activity on your network!.
SureLog SIEM supports “At the same time” operator, which is crucial for this detection.
https://surelog.medium.com/surelog-siem-at-the-same-time-operator-e2f64f2c826c
- File Monitor: Ransomware is designed to encrypt files, meaning that it will open, modify, and delete files one folder at a time. This type of anomalous activity can be detected by tracking file modification events (necessary for the encryption rewrites) and looking for processes that delete version shadow service (VSS) backups. SureLog SIEM uses its inbuilt alert rules to identify suspicious file activities.
- Abnormal Access to Confidential Data: Cybercriminals performing data theft focus on valuable and saleable data. Look for anomalous access to databases containing confidential information.
- Use Honeypot Folders to Detect Ransomware: The honeypot looks like a real computer system, with applications and data, fooling cybercriminals into thinking it’s a legitimate target. Place fake files with enticing names (such as a database file called credit cards) alongside valuable data and track access to this fake data. Any access attempts indicate an attack since no legitimate uses for the data exist.
- Unusual Activities: An unusual amount of file transfers to a single server, or an unusual number of new network shares added to a single server are often signs of staging activity
- Unusual Traffic: After finding valuable data, cybercriminals need to get it out of the network to sell it. Look for large-scale data transfers leaving the network.