As we know SIEM solutions are critical needs for cyber security and also for SOC. But the workload of security analysts/SOC operators/SIEM operators is increasing every single second. In a point of view SIGMA is one of the most useful methodology that helps to detect simple & complex security issues.
Detecting security breaches inside an infrastructure is heavily based on analyzing and monitoring events using logs. There are different types of logs, aggregation systems, strategies and technologies that help SOC analysts in their day to day job. While it’s excellent that there are a wide range of tools SOC teams and organizations can implement in their security posture, it also complicates the process of sharing information and knowledge within the organization and the community — each SIEM has its own query syntax (or language) and each log has it’s own unique fields.
Often analysts create rules to detect active threats or attacks and organizations would want to use them to alert upon a possible breach. For example, we might have an excellent rule to detect the creation of a specific malicious process and we want to share the rule with the community, partners, or clients. Having said that, sharing detection rules for behavior is complicated because each organization has its own way to digest logs, infrastructure and tools, so it might be more challenging for them to understand the rules and to integrate them into existing infrastructures.
The solution is SIGMA rules!
What is SIGMA?
Sigma is a generic and open signature format that allows you to describe relevant log events in a straightforward manner. The rule format is very flexible, easy to write and applicable to any type of log file.
Why SIGMA:
• It enables analytics to re-use and share across the organizations.
• High-level generic language for analytics
• The most reliable method such as solving the logging signature problem
• Plain text YAML files
• Easy Schema
• Thousands of proven rules library
Signatures are the staple of threat detection. The Sigma rule format has emerged in recent years to fulfill this role for event logs and has become increasingly popular in security operations and threat hunting communities.
Every SIEM vendor has their own specific language. However, The Public Sigma project provides rules and tooling for conversion into various SIEM provider alerting formats. It is not a match engine, so users are still expected to deploy a log management solution. In many cases, this is not ideal and real-time integration into existing log streams would be preferred.
The most powerful reason of SIEM preference is the real time correlation, no doubt on that. So, it would be more helpful to run SIGMA rules in real time instead of converting them to vendor specific SIEM language for the security analysts.
Supplying correlation rules that are tested by our Labs team prior to release, SureLog ensures that the detection content you use is effective and reliable.
Besides SureLog specific correlation rules, SureLog utilizes SIGMA rules for both detection and prevention layers.
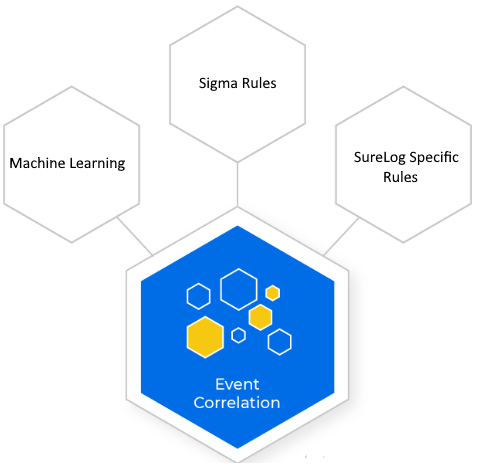
SureLog SIEM has always detects in real-time, and now Sigma rules do too. SureLog SIEM is the only SIEM that is fully compliant with Sigma Rules and capable of running them all with no performance hit and in real-time.
SureLog SIEM is the only SIEM that is fully compliant with Sigma, the open-source standard in SIEM rules. SureLog SIEM can run all Sigma rules simultaneously without a performance hit. There is no conversion of rules, nor is there down selection. The rules analyze data as it enters the system, always creating real-time alerts, meaning zero-mean time to detection (MTTD). SureLog SIEM is even compatible with the proposed features of Sigma.
This means that your analysts benefit from the largest community of open-source researchers for log analysis. SureLog SIEM watches data as it is collected, while traditional SIEMs store data and then search a database to detect with Sigma rules.
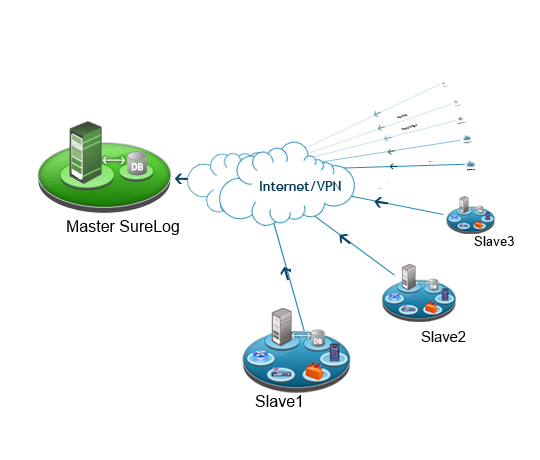
Real-time sigma rules enhanced distributed-correlation based thread detection with SureLog SIEM
Real-time correlators are CPU-intensive, aggregators are memory-intensive, and the persister is I/O-intensive. Distributed correlation, on the other hand, enables organizations to scale out their SIEM in a number of different ways, allowing it to meet the most demanding needs and the most complex use cases.
With Distributed correlation, customers can scale up to thousands of rules and thousands of EPS (events per second).
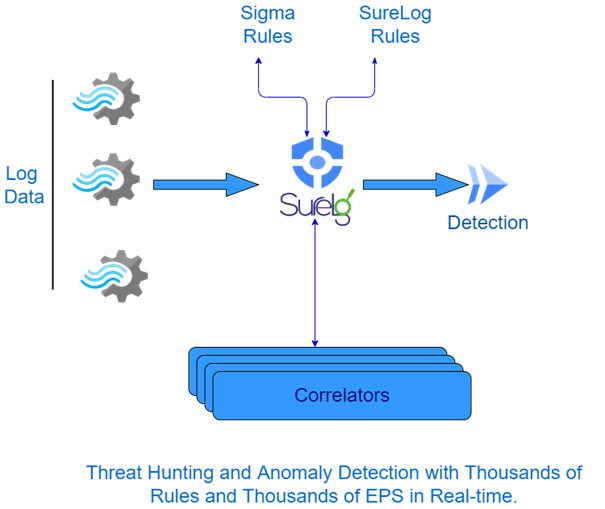
SureLog SIEM distributed correlation architecture runs real-time sigma rules and SureLog SIEM correlation rules that are more than 3000 rules in parallel. This means that SureLog SIEM distributed-correlation architecture supports sigma rules but not only sigma rules also support custom rule development.
SureLog SIEM runs thousands of rules against your audit data as it streams into SureLog SIEM. Rules can be as Simple as a Sigma Rule or as complex as a stateful model (SureLog rules). SureLog SIEM alerts in real-time when an incoming event triggers a hit. There is no searching of a database or delays in running scheduled searches.