Cyber Criminals are using various malicious tools for cyber-attacks based on the target’s strength to infiltrate the sensitive data and more often nowadays Publicly Available Hacking Tools are mainly used by threat actors for various attacks around the world. Here we can see the most used top 4 publicly available hacking tools by threat actors [1]:
• China Chopper
• Mimikatz
• PowerShell Empire
• HUC PacketTransmitter
Those tools are well-known type of [2]
• Webshells
• Credential Stealers
• Lateral movement frameworks
• Command and control (C2C) obfuscators
SureLog SIEM detect those hacking tools and create alert to inform what is going on the remote system.
SureLog uses learned behavior as a baseline and detect if any learned activity detected.
Each attack type analyzed and attack behavior like loaded DLLs and the sequence of request are used to create a bad behavior baseline. Than SureLog searched for this baseline to detect attacks
C:\Windows\System32\advapi32.dll C:\Windows\System32\rpcrt4.dll
C:\Windows\System32\crypt32.dll C:\Windows\System32\rsaenh.dll
C:\Windows\System32\cryptdll.dll C:\Windows\System32\samlib.dll
C:\Windows\System32\gdi32.dll C:\Windows\System32\sechost.dll
C:\Windows\System32\imm32.dll C:\Windows\System32\secur32.dll
C:\Windows\System32\kernel32.dll C:\Windows\System32\shell32.dll
C:\Windows\System32\KernelBase.dll C:\Windows\System32\shlwapi.dll
C:\Windows\System32\msasn1.dll C:\Windows\System32\sspicli.dll
C:\Windows\System32\msvcrt.dll C:\Windows\System32\user32.dll
C:\Windows\System32\ntdll.dll C:\Windows\System32\vaultcli.dll
Figure 1. List of DLLs that are used as a baseline to detect Mimikatz versions
When SureLog detects unusual activity, like an unusually DLLs loaded for a particular type of attack, it generates an alert. These baselines are also continuously updated to avoid generating an unacceptable number of false positives.
SureLog utilizes Sysmon Event ID 7
Image loaded:
UtcTime: 2017-04-28 22:45:16.662
ProcessGuid: {a23eae89-c5fa-5903-0000-0010bf439000}
ProcessId: 12536
Image: C:\Windows\System32\notepad.exe
ImageLoaded: C:\Windows\System32\ole32.dll
Hashes: SHA1=B2A2BBCFB69B1F0982C4B82055DAD9BAE4384E4B
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
If SureLog detects any attack type of
• China Chopper
• Mimikatz
• PowerShell Empire
• HUC PacketTransmitter
In SureLog, we could build a baseline of all DLLs executed on all monitored systems over a period of time, and then detect any pattern used by the above attack types.
Detected attack type will be written to “SoftwarePackage” and the process name file will be written to “ServingProcess” field, and “Installoperation” will set to 6
There is also correlation rule to detect attacks in real time. SureLog creates alerts and takes action if any attack detected.
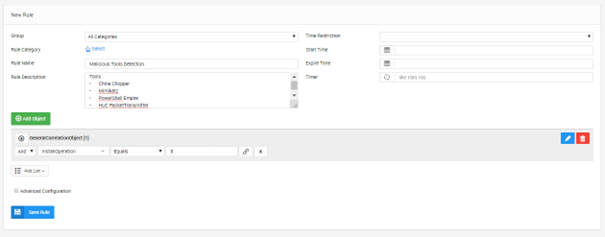
Figure 2. SureLog Malicious Tools Detection Rule
References
1. https://www.securitynewspaper.com/2019/05/03/top-5-tools-used-by-cyber-criminals-recently/
2. https://gbhackers.com/these-are-the-top-5-publicly-available-hacking-tools-mostly-used-by-hackers/
3. https://cyberwardog.blogspot.com/2017/03/chronicles-of-threat-hunter-hunting-for.html