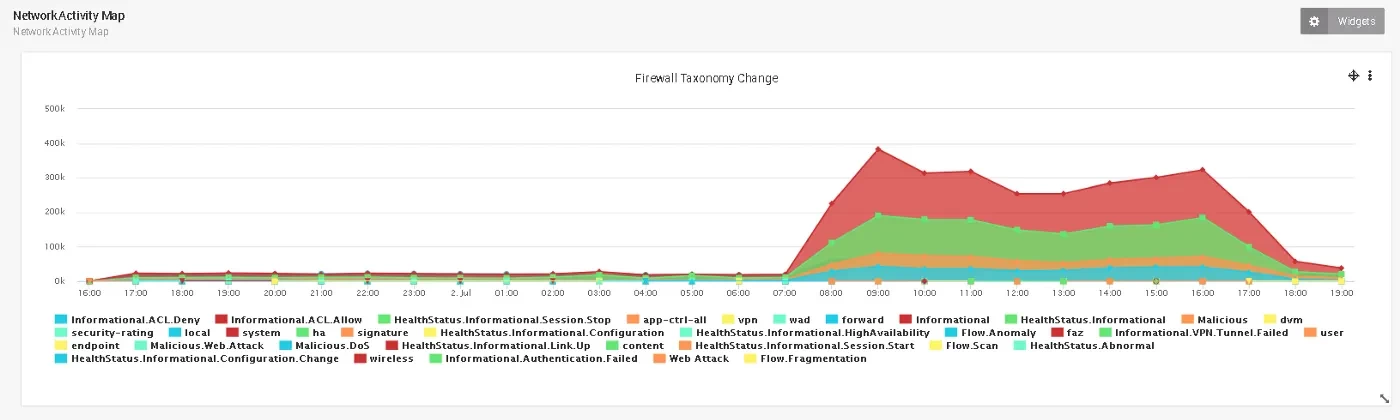
There are malware tools available that can create Windows services with random service names and descriptions. Emotet infection is an example of malicious services created on the machine. This is due to how Emotet installs itself on a machine, creating randomly named numeric services, which in turn try to run another randomly named executable in C:\Windows [1]. The example below shows four Emotet services (other may have more) that have been created on an infected machine.
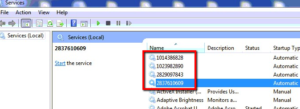
Figure 1. Malicious Service
Numerous malware families also create registry keys for persistence with randomized key names and values [2]. Filenames are also may be an indicator of malware [3,4]. Also Emotet s utilize random file names. Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the costliest and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors.
One last example is process names; often malware will put itself, randomly named, into a randomly named folder in AppData. There are actually two potential applications here: one for the name of the binary itself, and one for the randomly named folder in which it resides [5].
Monitoring for infected files
• C:Windows
• C:Program Files
• C:\Windows\ProgramData
• C:Users/[current user]/AppData
• C:Users/[current user]/AppData/Roaming
• C:Users/[current user]/AppData/Roaming/Microsoft
• C:/Windows/SysWOW64
• …..
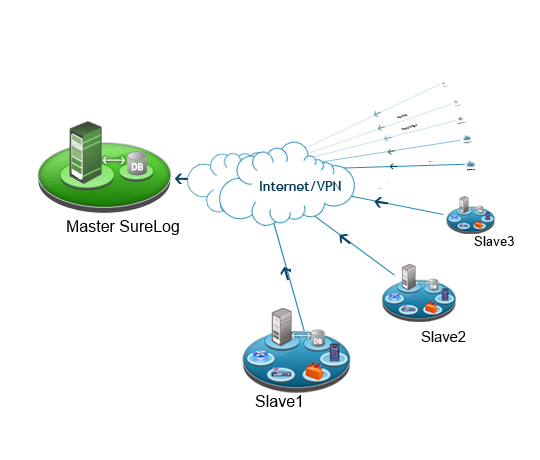
SureLog detects randomly-named files, registry keys, services and processes (Both created and spawned by) in real time.
SureLog utilizes:
Event ID 7045 – A service was installed in the system
Event ID 4688 – A new process has been created
Event ID 4656 – A handle to an object was requested. File and Registery
Event ID 4697 – A service was installed in the system
Sysmon [7]
And in Linux, just monitor /var/log/audit/audit.log file.
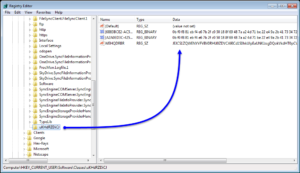
Figure 2. Malicious Registry Key
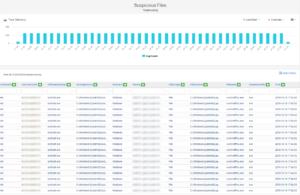
Figure 3. SureLog Suspicious File Detection Reports
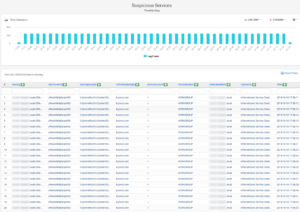
Figure 4. SureLog Suspicious Services Detection Reports
Suspicious processes, files and services are detected in real time and depicted to the InstallOperation field on the SureLog schema. SureLog utilizes ML to detect suspicious processes, files and services.
![]()
Figure 5. SureLog Related Rules
References
• https://community.sophos.com/kb/en-us/127218
• https://www.tripwire.com/state-of-security/mitre-framework/evade-detection-hiding-registry/
• https://community.spiceworks.com/topic/2168878-remove-new-emotet-trickbot-malware
• https://blog.talosintelligence.com/2019/08/threat-roundup-0726-0802.html
• https://www.dell.com/support/article/tr/tr/trdhs1/sln285424/security-scanner-malware-removal-guide?lang=en
• https://labs.jumpsec.com/2019/02/06/enhanced-logging-to-detect-common-attacks-on-active-directory-part-1/
• https://www.sans.org/cyber-security-summit/archives/file/summit-archive-1554993664.pdf
• https://www.cybereason.com/blog/triple-threat-emotet-deploys-trickbot-to-steal-data-spread-ryuk-ransomware
• https://securityboulevard.com/2019/06/security-alert-fin8-is-back-in-business-targeting-the-hospitality-industry/
• https://www.binarydefense.com/trickbot-ono-new-tricks/
• https://blog.malwarebytes.com/detections/trojan-emotet/