Lists are available in most (if not all) SIEMs. Lists are different in each of the SIEMs on the market. Some are simply a single column which you can use for e.g. IP Addresses, and others are up to 10000 columns that can support a significant amount of data.
This article may interest you SQL Streaming Based Thread Detection in SureLog SIEM

Why Watchlists?
Why do you need to look up information in a SIEM query, whether hunting queries or detection rules? The top reasons are:
- Overcoming limitations of Real-Time Rule Engines — SIEMs with real-time rule engines have the advantage of triggering your use cases as data is ingested (versus running a query every 5 minutes). But the real-time advantage turns out to be a disadvantage when you have a use case that spans a greater timeframe. The longer the timeframe of the use case, the more system resources used by the real-time engine, thus making some use cases impossible. For example, real-time rule engines can easily detect 10 or more failed logins in 24 hours, but not over three months–that would be far too much data to keep in memory. To compensate for this, Lists can be used to store data required by use cases that can’t be done via the real-time rule engine.
- Keeping rule states- For example, you can put the result of the first use case into a List, and then use a second use case that uses both the real-time engine and values in the List.
- Enrichment — extending events or alerts with additional information needed for detection or investigation. Common enrichment sources include user information, asset or resource information, geoinformation, and threat intelligence.
- Allow-listing — making sure a query ignores known outliers that do not justify alerting on. For example, excluding a backup process from a query identifying access to large amounts of data.
- Watch lists — in reverse, ensure that alerts with the listed entities are promoted, whether by assigning a higher severity or by alerting only on those. For example, flagging access to sensitive finance files.
- Investigate threats and respond to incidents quickly with fast import of IP addresses, file hashes, etc. from csv files. Then utilize the watchlist name/value pairs for joining and filtering for use in correlation rules and threat hunting.
- Import business data, such as user lists with privileged system access as a watchlist. Then use the watchlist to create allow and deny lists. For example, use a watchlist that contains a list of terminated employees to detect or prevent them from logging in to the network.
- Create allow-lists to reduce alert fatigue. For example, use a watchlist to build an allow list to suppress alerts from only a limited set of IP addresses to do specific functions and thus removing benign events from becoming alerts.
Those are critical capabilities of a SIEM. While each specialized security tool has a partial view of the world, a SIEM can utilize its broader outreach to enrich the event and alert data and centrally manage allow-lists and watch lists.
As you can see, Lists can be very useful for SIEM end users. Overlooking List functionality during a SIEM design can have profound impacts. While List functionality differs per SIEM, it’s important to understand how your SIEM works and ensure it meets your requirements.
SureLog List Management
SureLog EE Edition supports different types of lists.
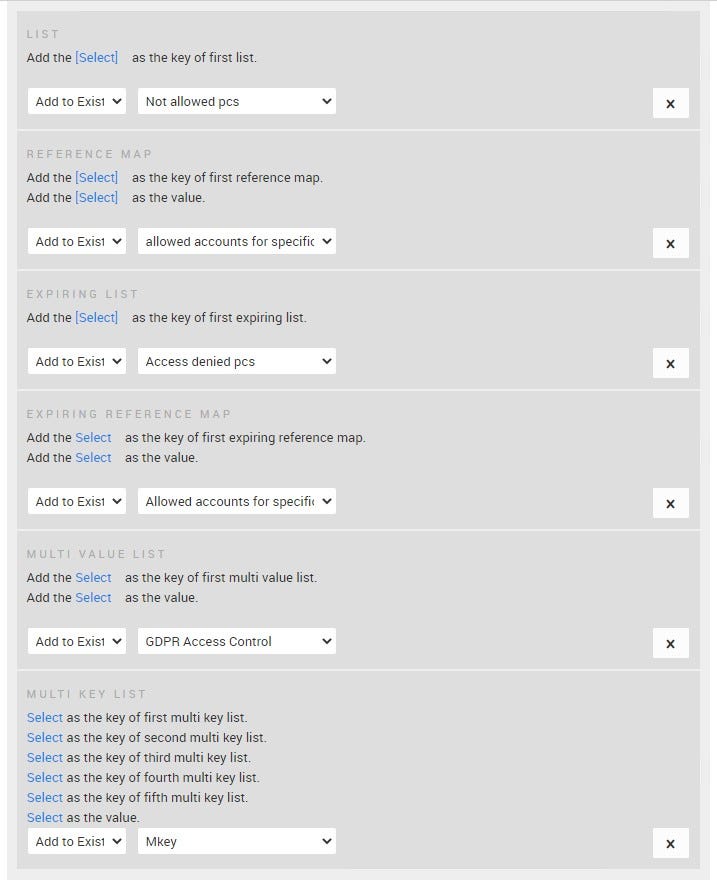
Lists: Use a list to compare a property value against a list, such as IP addresses or user names.
Reference Maps: Use a reference map to verify a unique combination of two property values. Example: To correlate user activity on your network, create a reference map that uses the LoginID parameter as a key, and the Username as a value.
Expiring Lists: When an Expiring List is being created, you can choose to either use a static TTL for the entries that will delete them after a specific period or manage them yourself and delete entries manually.
Expiring Reference Maps: Reference map with a TTL.
Multi Value Lists: A collection of data that maps a key to multiple values (up to The only SIEM products with such list types are SureLog, Qradar and Arcsight.values). Every key is unique and maps to multiple values. Example: To test for authorized access to a patent, create a multi value list that uses a custom event property for Patent ID as the key, and the Username parameter as the value. Use the multi value lists to populate a list of authorized users.
Multi Key Lists: A Multi key list allows multiple map keys (up tp 5 keys) to be merged together. Example Create a multi key list that stores Username as the first key, Source IP as the second key, Destination IP as the third key, and Source Port as the value.
List operators are another critical feature of SIEM list management. SureLog EE has advanced list operators like counting, summing list items also time diff check operator.
The content has been sourced from





