Spearphishing Link (T1192)
Spearphishing with a link is a specific variant of spearphishing. It is different from other forms of spearphishing in that it employs the use of links to download malware contained in email, instead of attaching malicious files to the email itself, to avoid defenses that may inspect email attachments.
Case 1:
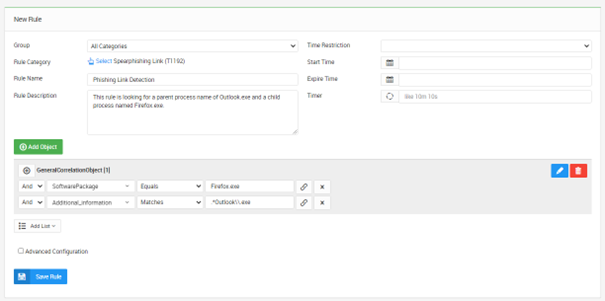
This use case works to detect when someone clicks on a link in Outlook.
Rule 1:
This rule is looking for a parent process name of Outlook.exe and a child process named Firefox.exe. The process name would be expanded upon based on the browsers in your environment. The rule leverages a log source type of Microsoft Sysmon, where event ID 1 will record the process execution of Outlook spawning Firefox and passing the URL in the command line.
Masquerading (T1036)
Masquerading [1] occurs when the name or location of an executable, legitimate or malicious, is manipulated or abused for the sake of evading defenses and observation. Several different variations of this technique have been observed.
SureLog SIEM library has two rules to detect variations of masquerading in Windows.
Case 1:
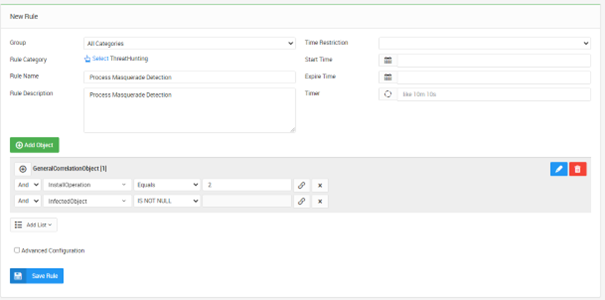
A popular technique for hiding malware running on operating systems is to give it a name that’s confusingly similar to a legitimate operating system process, preferably one that is always present on all systems. Processes whose names are confusingly similar to those of critical system processes are likely to be malicious. Malicious process detection using process name is critical.
Rule 1:
SureLog detects in real-time if there are any malicious processes in the system. Detected malicious processes will be written to “Servingprocess” and the original file will be “Infectedfile” field, and “Installoperation” will set to 2. [2]
Case 2:
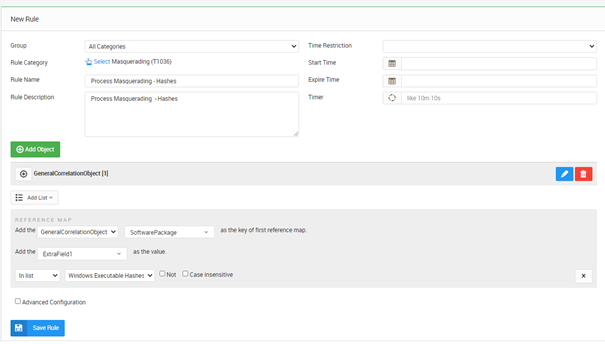
ATT&CK describes several variations of masquerading, but Masquerading as Windows LSASS process is a great example where cmd. exe is copied to c:\windows\system32\temp and renamed to lsass.exe. It’s then used to run arbitrary commands and executables, but in logs and process queries, it will look like the trusted processes Local Security Authority System Service showing up in logs as c:\windows\ system32\temp\lsass.exe which is very close to c:\windows\system32\temp\lsass.exe
Rule 2:
First, you must generate a list of hashes of all the executables in the system root using a PowerShell script: get-childitem c:\windows\system32 -recurse|where {$_.extension -eq ‘.exe’}|Get-FileHash -Algorithm md5|select hash|Out-File ‘.\hashes.txt’ That file is imported as list in SureLog. Then the SureLog Rule looks for Microsoft Sysmon Event ID 1 – Process Creation where the executable’s hash is on the list but resides outside the system root. The hash list needs to be updated as Windows executables are patched.
References
1. https://attack.mitre.org/techniques/T1036/
2. http://anet-canada.ca/2019/10/12/hunting-critical-process-masquerade-using-surelog-siem/