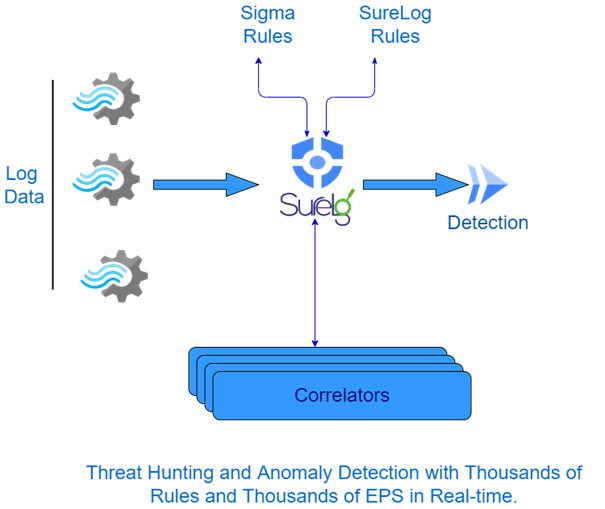
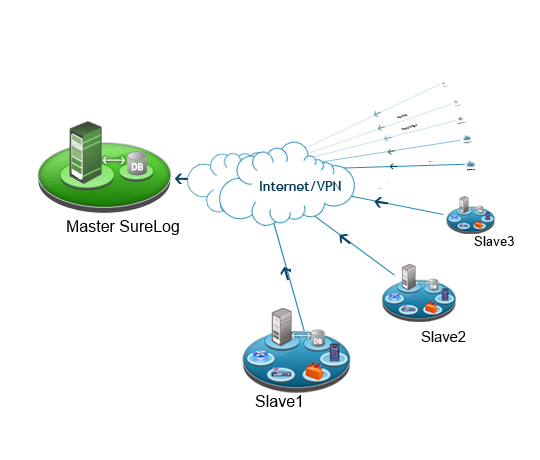
There are many recommendations and regulations mandating long-term hot, online, immediately available, and live logs. From a security point of view, the purpose of a log is to act as a red flag when something bad is happening.
“11 Strategies of a World-Class Cybersecurity Operations Center” by MITRE suggests a minimum of six (6) months to 2+ years of online log retention within the SOC, recognizing the distinct needs of SOC triage analysts, SOC forensics/investigations analysts, and external audit and investigation support [1].
The Memorandum for the Heads of Executive Departments and Agencies, published by the Executive Office of the President, Office of Management and Budget (Improving the Federal Governments Investigative and Remediation Capabilities Related to Cybersecurity Incidents), mandates 12 Months of Active Storage (hot log) and 18 Months of Cold Data Storage [2].
Event Logging Guidance from the Treasury Board of Canada Secretariat established log retention times of 90 days to two years [3].
In addition, real-world attack cases mandate long-term hot logs. The timeline of the SolarWinds hack demonstrates the criticality of hot-log usage in detecting and responding to cyberattacks.
The hack began in September 2019 when threat actors gained unauthorized access to SolarWinds’ network. More than 18,000 SolarWinds customers installed the malicious updates, with the malware spreading undetected.
However, the attack went undetected for many months until December 2020. Here is the timeline of the SolarWinds hack:
• September 2019: Threat actors gain unauthorized access to SolarWinds’ network
• October 2019: Threat actors test initial code injection into Orion
• Feb. 20, 2020: Malicious code known as Sunburst injected into Orion
• March 26, 2020: SolarWinds unknowingly starts sending out Orion software updates with hacked code
The SolarWinds hack was first detected in December 2020.
Data breaches were a wake-up call for organizations around the world, highlighting the critical importance of robust cybersecurity measures and effective incident response plans. One key component of these measures is the use of live logs to monitor network activity and detect potential threats in real-time.
While there are challenges associated with live log monitoring, the benefits far outweigh the risks. By investing in the right tools, technologies, and personnel, organizations can better protect themselves against cyberattacks and reduce the risk of costly data breaches.
Furthermore, many “Request for Proposals (RFPs)” require that logs, even if stored in an archive, must be made available within 24 hours [4]”. It’s not possible to retrieve logs within 24 hours from the last 6 months (180 days) unless they’ve been kept live.
Google expresses the importance of the issue as follows: “So. Conclusion: 1 year log retention is both a boring compliance requirement and a key resource for detecting top-tier threats [5].”
Therefore, it is crucial for organizations to implement a logging and monitoring strategy that aligns with the recommendations and regulations mentioned above. By keeping logs hot, online, and immediately available, organizations can detect potential threats in real-time and respond to incidents quickly, reducing the risk of costly data breaches.
Moreover, having a long-term log retention policy can also assist in conducting forensic investigations and compliance audits. It can provide a historical record of events that can be useful for identifying the root cause of incidents and demonstrating compliance with regulatory requirements.
In conclusion, live log retention is an essential component of a robust cybersecurity strategy. It can help organizations detect and respond to cyber threats in real-time, assist in conducting forensic investigations and compliance audits, and demonstrate compliance with regulatory requirements. By following the recommended retention periods and implementing the appropriate tools and technologies organizations can better protect themselves against cyberattacks and reduce the risk of costly data breaches.
Keywords: MITRE, Government, USA, Canada, Solarwinds, Google, RFP, Regulations, Recommendations
References:
4. http://vadodarasmartcity.in/vscdl/assets/tenders/17.09.2020/2021_499-1.pdf
5. https://chroniclesec.medium.com/retaining-logs-for-a-year-boring-or-useful-9b04c1e55fba